People receive a lot of e-mails in their mail boxes on a daily basis. Some of them are interesting and relevant to them, while others are not. Some aim to inform the recipient and others…well they simply want to harm the recipient, like for example the e-mail depicted in the image. Before diving into the analysis, it should be stated that all identifiable details (IP addresses, contact person details, phones, hacked sites, targeted bank etc) have been anonymized (eg. the targeted bank’s name is replaced with the fictitious Phishing-target bank) in order to prevent any unnecessary disclosure of information and to respect the real bank’s wish, who did not want its’ name to be mentioned as a target of a phishing campaign.
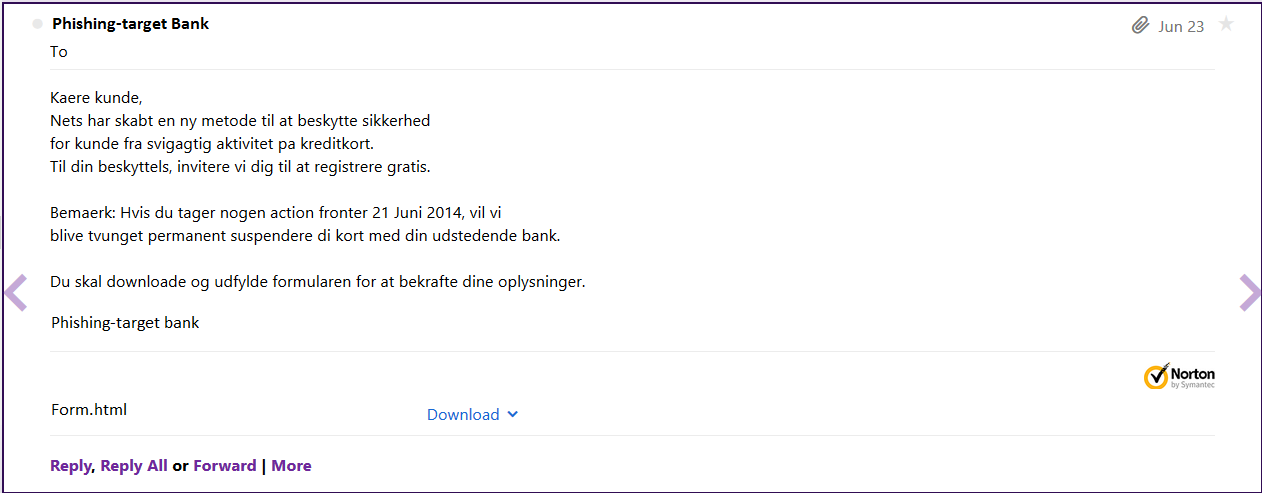
Received e-mail
Let’s take a look. Since I do not speak Danish, I ‘ll use Google translate service (https://translate.google.com/) to see what it says.
Wow it says that if I don’t download and complete the attached form by 21st June my credit card will be suspended!!!
From Phishing-target Bank Mon Jun 23 03:46:31 2014
Dear customer,
Nets have created a new method to protect the safety
the customer from fraudulent activity on credit cards.
For your protection IC, we invite you to register for free.
Note: If you take no action fronts June 21, 2014, we will
be forced to permanently suspend your card with your issuing bank.
You must download and complete the form to confirm your information.
Phishing-target Bank
Translated message
Translated message
Well, if I am a customer of Phishing-target bank, I am alarmed.
Is this an e-mail actually coming from Phishing-target Bank (http://www.phishing-targetbank.dk/)? Should I download and complete the form?
How can I be sure that this e-mail is not malicious?
Well, first of all who is the sender?
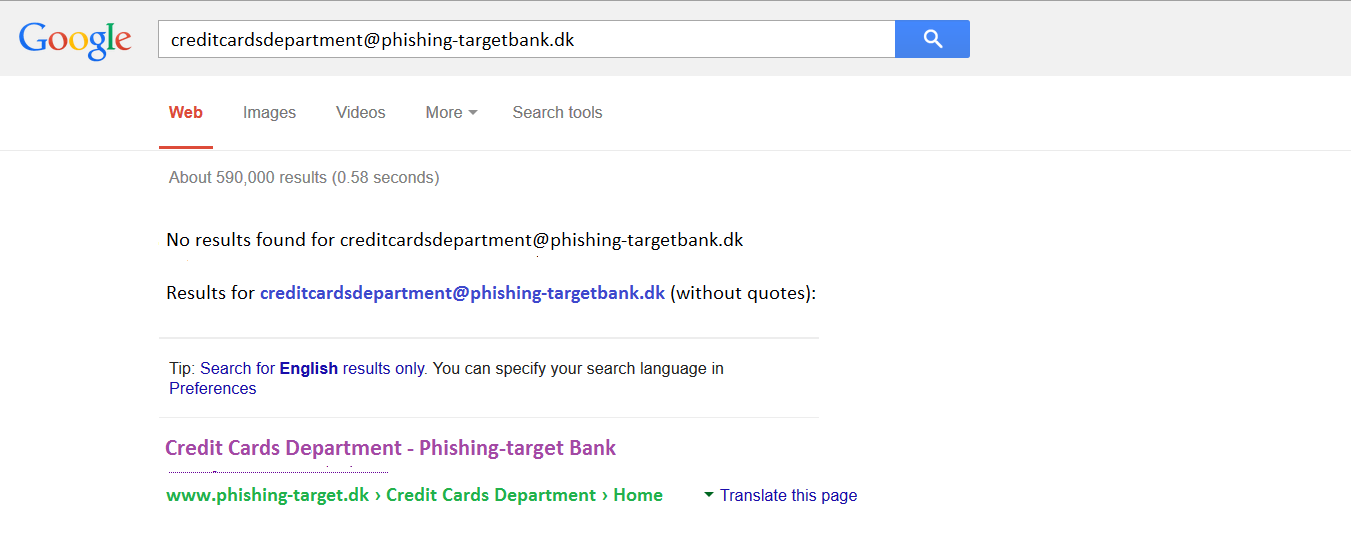
The e-mail has been sent from “Phishing-target Bank <creditcardsdepartment@phishing-targetbank.dk>”. Is this a real Phishing-target bank e-mail? If it is, Google might know it….
At this point I search the sender’s e-mail address using Google…
Google search results for “creditcardsdepartment@phishing-targetbank.dk”
Google does not know this e-mail, but there is a Credit Cards department within the Phishing-target bank group (www.phishing-target.dk/credit%20cards%20department/home.html).
At this point I visit the credit cards department page…
Well, if the bank was real, I would see that the Phishing-target bank group has a credit cards department, which, among others, deals with suspending customers’ credit cards. But does the credit cards department have an e-mail? Could they inform a customer about his / her card? Would they do that? How can a customer find out? The most obvious and “safe” answer would be phone the bank and ask them about it…”Hello, I am your customer, did your credits card department send me an e-mail about suspending my card?”
At this point Phishing-target ‘s employee on the phone would be alarmed and tell the customer that their bank will never inform them by e-mail about suspending his / her card.
In such cases, the first step of the investigation is finding out where the e-mail actually came from. How do we do that? Well…we can examine the e-mail header.
From Phishing-target Bank Mon Jun 23 03:46:31 2014
X-Apparently-To: xxxxxxxxxxxx@yahoo.com via 10.194.14.47; Mon, 23 Jun 2014 10:46:36 +0000
Return-Path: <creditcardsdepartment@phishing-targetbank.dk>
Received-SPF: permerror (encountered permanent error during SPF processing of domain of phishing-target.dk)
ZSB0aWwgYXQgYmVza3l0dGUgc2lra2VyaGVkIGZvciBrdW5kZSBmcmEgc3Zp
Z2FndGlnIGFrdGl2aXRldCBwYSBrcmVkaXRrb3J0LiBUaWwgZGluIGJlc2t5
dHRlbHMsIGludml0ZXJlIHZpIGRpZyB0aWwgYXQgcmVnaXN0cmVyZSBncmF0
aXMuIEJlbWFlcms6IEh2aXMgZHUgdGFnZXIgbm9nZW4gYWN0aW9uIGZyb250
ZXIgMjEgSnVuaSAyMDE0LCB2aWwgdmkgYmxpdmUgdHZ1bmdldAEwAQEBAQN0
ZXh0L3BsYWluAwMxAk55a3JlZGl0Lmh0bWwDYXBwbGljYXRpb24vb2N0ZXQt
c3RyZWFtAwM0
X-YMailISG: 8gLwCRoWLDs4NzGA9bf11hscXKF8mHYT3YFCKU0J7BF7EvyR
FI1jU7.b6bglR4dCo6Pl.09nhfQZf0UxdR3rYSbz0G1VDH9eVoGZ16UHDNgO
gde32Aanl32aHOpRJ4qwvJmwRLVFLO7XUMB_j5QYpTOk.ewsQNmMXSDq4Cvz
AvM0gn8PA9ZGJ040wfmafJSNFmvugD8Ze_O3ucVQCcZG.RpDobJZP5.i5tNa
RdbaIBY43hioeN3T_6qFipDWJHn_WoWDepnsqpo_FGnL4GlGczKopdksDX3.
PbXIbOa_ew4RJOCZqVv0wNJb8s_A7ZXc.VuNDP70J4y_eoARYDxysMAbktUh
7ZL1CGO6VDEEUeJnlRhpCDi8GKVwkqVxBqnrBVQPR8ob_4ped8mpmC0ytnqB
BlpppLF5BdTq9lYMyDNoWh1r5dKAmcIS3948Fs.ZyypRBNAdjE3R1YfSDf4J
mD8ZqbvONV01EzZ1ZQj2TAgRTXlyuTkZC_jAo476hicB9N4km4_njQak_XgG
QzK.HKImek29R09Q94kChVNbaeH5CJAoCkdgyiK3pG_sdRH1u2mRhM_5buWy
pzUBpFjm6n6IMiYdOGOaTUoLkWDW7WX9BApLHizV91KBLh2U7ZUGAoELy6ed
Chnq4X8s3p9pmWg4YQIJ3HQkuRAAtVYcfIiO02Jp2gk9UhVUBFVpzy5E6kB8
4Gh.1u9IYUS2CgAWfKQCl05ZLE3Jd3IM5wmejHbfub0AXCGZlXtMrvWUuPJH
UN_ieV12Ko2iswOcGB6vFWdA1CABD0IRtpNrmLgpnkTvRnGdH_GnHLohZy3k
_2SCNC4gSW4Rr3B54F6mTj9KdMSoKpAvRCn0enNshuUvHvSnzQGQ38V2tPAz
ugpub1LdUHNtZ.pYm0uAujDsbmIBJI8TRqJs5TnVX_UvqV4uEenXxn9QIAKl
89vHkMkVxDYCpE7latQ_Oeotj6n3wa6aP6uZTgcP4gNZ2VPlplFx_PiUrD_G
k8DvqHDV10lDh80Pj9wBB11R84zSzZlwlTtMCvMQRxvw7mYtm.TGAyDaMimU
jtPclEff7ca9lwK6y0e_AhYjueYTd0.PuEtoyAuYNoykDVp1SM7xQtM3Hqym
lzqi3tkujWJVcW1nO0Lzof1qjwq9bgPSGz7Um9Ta7eeHPqAxdq8Fk1ZFbqSj
V13kVS9GSZT1Pi4dow4sCB9OAwr8ngKqHoOVLgGw1yrRnShw_vmL3ijkjime
mZi2FMOUrJUzcH6R98CtXu27htfhuCVvVxikxgeypix2jzuuaYW7gp.fAhIV
CygPXPYUt6NF.5O.CPdQc12nW9QK2R4jZ7pdgoPLUYXn2X5pWQmw6TWPb7A9
zlvUKAs-
X-Originating-IP: [xx.xxx.xxx.170]
Authentication-Results: mta1252.mail.ne1.yahoo.com from=phishing-targetbank.dk; domainkeys=neutral (no sig); from=phishing-targetbank.dk; dkim=neutral (no sig)
Received: from 127.0.0.1 (EHLO xxxx.ru) (xx.xxx.xxx.170)
by mta1252.mail.ne1.yahoo.com with SMTP; Mon, 23 Jun 2014 10:46:33 +0000
Received: from localhost ([127.0.0.1] helo=User)
by xxxx.ru with smtp (Exim 4.72)
(envelope-from <creditcardsdepartment@phishing-targetbank.dk>)
id 1Wz1lf-0005y5-6P; Mon, 23 Jun 2014 14:46:31 +0400
From: “Phishing-target Bank”<creditcardsdepartment@phishing-targetbank.dk>
Subject: Phishing-target : suspendere kreditkort
Date: Mon, 23 Jun 2014 03:46:31 -0700
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary=”—-=_NextPart_000_005C_01C2AA85.68872A44″
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2800.1081
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2800.1081
Content-Length: 4731
E-mail header
So, I am a customer of a Danish bank and I received an e-mail supposedly from them. I suppose I would expect the e-mail to originate from an IP address registered to Phishing-target bank. Does it?
The X-Originating-IP is the e-mail header field that can tell us the IP of the computer / person that sent the email. So what does the received e-mail tell us? Well it tells us that it came from IP address xx.xxx.xxx.170. Where is this address located?
Using my favorite WHOis service (whois.domaintools.com) I see it is located in “Irkutsk, Russian Federation“.
IP Information for xx.xxx.xxx.170
QuickStats
IP Location
Russian Federation Irkutsk IspsystemCjsc
ASN
AS29xxx ISPSYSTEM-AS ISPsystem, cjsc,LU (registered Jun 23, 2003)
Whois Server
whois.ripe.net
IP Address
xx.xxx.xxx.170
Reverse IP
76 websites use this address.
inetnum: xx.xxx.xxx.0 – xx.xxx.xxx.255
netname: THEFIRST-NET
org: ORG-FVDS1-RIPE
descr: TheFirst-RU customers (WebDC Msk)
country: RU
admin-c: AB11xxx-RIPE
tech-c: ST63xx-RIPE
status: ASSIGNED PA
mnt-by: ISPSYSTEM-MNT
mnt-by: THEFIRST-MNT
source: RIPE # Filtered
organisation: ORG-FVDS1-RIPE
org-name: CJSC THE FIRST
org-type: OTHER
address: CJSC The First, xxxxxxxx
address: PoBoxxx, Irkutsk, xxxxxx
address: Russian Federation
abuse-mailbox:
mnt-ref: THEFIRST-MNT
mnt-by: ISPSYSTEM-MNT
source: RIPE # Filtered
person: Contact Person 1
address: xxxxxxxxxxx
address: Irkutsk, xxxxxx, Russian Federation
phone: +7 3952 xxxxxx
nic-hdl: AB11xxx-RIPE
mnt-by: ISPSYSTEM-MNT
source: RIPE # Filtered
person: Contact Person 2
address: xxxxxxxxxxx
address: Irkutsk, xxxxxx, Russian Federation
phone: +7 3952 xxxxxx
nic-hdl: ST63xx-RIPE
mnt-by: ISPSYSTEM-MNT
source: RIPE # Filtered
route: xx.xxx.xxx.0/23
descr: TheFirst-RU
origin: AS29xxx
mnt-by: THEFIRST-MNT
source: RIPE # Filtered
IP WHOis information
If we want to analyze the e-mail header a little further we can use my favorite online e-mail tracer and track the course that the e-mail took before it reached our mailbox.
The contact information of the ISP for the above IP address is:
The mail appears to be originated from the computer with IP
address xx.xxx.xxx.170 (xxxx.ru).
The contact information of the ISP for the above IP address is,
+7 3952 xxxxxx
Contact Person 2, Irkutsk, xxxxxx, Russian Federation
RUSSIA
The sender’s email address is creditcardsdepartment@phishing-targetbank.dk
The message-id of the the mail is <>.
Path traced by the mail
creditcardsdepartment@phishing-targetbank.dk
Mon, 23 Jun 2014 03:46:31 -0700
localhosthelo=User(127.0.0.1)
Mon, 23 Jun 2014 14:46:31 +0400
127.0.0.1(xx.xxx.xxx.170)
Mon, 23 Jun 2014 10:46:33 +0000
mta1252.mail.ne1.yahoo.com
G.RpDobJZP5.i5tNa
ReceivedBy
ReceivedFrom
Date
G.RpDobJZP5.i5tNa
mta1252.mail.ne1.yahoo.com
Mon, 23 Jun 2014 14:46:31 +0400
mta1252.mail.ne1.yahoo.com
127.0.0.1[xx.xxx.xxx.170]
Mon, 23 Jun 2014 10:46:33 +0000
127.0.0.1[xx.xxx.xxx.170]
localhosthelo=User[127.0.0.1]
Mon, 23 Jun 2014 14:46:31 +0400
localhosthelo=User[127.0.0.1]
creditcardsdepartment@phishing-targetbank.dk
Mon, 23 Jun 2014 03:46:31 -0700
Details obtained from Regional Internet Registry
Domain/Registrant
IP
Registry
Country
City/Address
ISP
127.0.0.1/xxxx.ru
xx.xxx.xxx.170/THEFIRST-NET
RIPE
RUSSIA
xxxxxxxx Irkutsk, xxxxxx, Russian Federation
THEFIRST-RU CUSTOMERS (WEBDC MSK)
xx.xxx.xxx.170/THEFIRST-NET% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the “-B” flag.
% Information related to ‘xx.xxx.xxx.0 – xx.xxx.xxx.255’
% Abuse contact for ‘xx.xxx.xxx.0 – xx.xxx.xxx.255’ is ‘abuse@ispsystem.com’
inetnum: xx.xxx.xxx.0 – xx.xxx.xxx.255
netname: THEFIRST-NET
org: ORG-FVDS1-RIPE
descr: TheFirst-RU customers (WebDCMsk)
country: RU
admin-c: AB11xxx-RIPE
tech-c: ST63xx-RIPE
status: ASSIGNED PA
mnt-by: ISPSYSTEM-MNT
mnt-by: THEFIRST-MNT
source: RIPE # Filtered
organisation: ORG-FVDS1-RIPE
org-name: CJSC THE FIRST
org-type: OTHER
address: CJSC The First, xxxxxxxxxx
address: PoBoxxx, Irkutsk, xxxxxxx
address: Russian Federation
abuse-mailbox: abuse@abusehost.ru
mnt-ref: THEFIRST-MNT
mnt-by: ISPSYSTEM-MNT
source: RIPE # Filtered
person: Contact Person 1
address: xxxxxxxxxxx
address: Irkutsk, xxxxxx, Russian Federation
phone: +7 3952 xxxxxx
nic-hdl: AB11xxx-RIPE
mnt-by: ISPSYSTEM-MNT
source: RIPE # Filtered
person: Contact Person 2
address: xxxxxxxxxxx
address: Irkutsk, xxxxxx, Russian Federation
phone: +7 3952 xxxxxxx
nic-hdl: ST63xx-RIPE
mnt-by: ISPSYSTEM-MNT
source: RIPE # Filtered
% Information related to ‘xx.xxx.xxx.0/23AS29xxx’
route: xx.xxx.xxx.0/23
descr: TheFirst-RU
origin: AS29xxx
mnt-by: THEFIRST-MNT
source: RIPE # Filtered
% This query was served by the RIPE Database Query Service version 1.73.1 (DB-3)
E-mail header analysis
Concluding, I have received an e-mail from a Danish bank group (Phishing-target) that was sent from Russia.
Thus far, I have enough to not download the form and report this e-mail as phishing to any of the online Anti-phishing sites (http://www.phishtank.com/, http://www.antiphishing.org/, etc).
It is worth noting here that even if the e-mail originated from an IP address in Denmark that was registered to the Phishing-target bank group it is recommended that the recipient phones the bank in order to be certain that he / she is not being phished. Banks do not usually notify customers by e-mail about suspending credit cards, changing account credentials, etc.
Is there anything else this e-mail can tell us? Hmmm, we have checked the body, the header…Did we check the attachment? The mail asked the recipient to download a form, did it not?
In part 2 of the article we will see what the form can tell us….
DISCLAIMER
This article is written for scientific purposes. It aims to:
- educate simple users on how to identify phishing e-mails and what they should be careful of in order not to get phished and
- educate more advanced users in phishers’ techniques and how these can be analyzed.